Everyone has antivirus, a firewall, and automated updates today. So how’s that working out?
The landscape has shifted dramatically since those protections were created and the evidence is in the headlines. There isn’t a day where there is not another organization in the news that has had their data ransomed or are otherwise breached. Something’s got to give.
Today’s challenge is bringing the alerts and preventative controls that automated tools deliver alongside expert competency to deliver real defense-in-depth. Security Operations Centers, or SOCs, are not new, but they are novel for many businesses. SOCs leverage systems that collect a significant amount of information computers, network devices, and programs share about what’s happening as they perform their tasks. And the staff of Security Operations Centers monitors for security events large and small that may indicate a malicious event is happening on their network. They pay attention to new vulnerabilities and the tactics, techniques, and procedures of malicious actors, integrating that knowledge into protecting client networks.
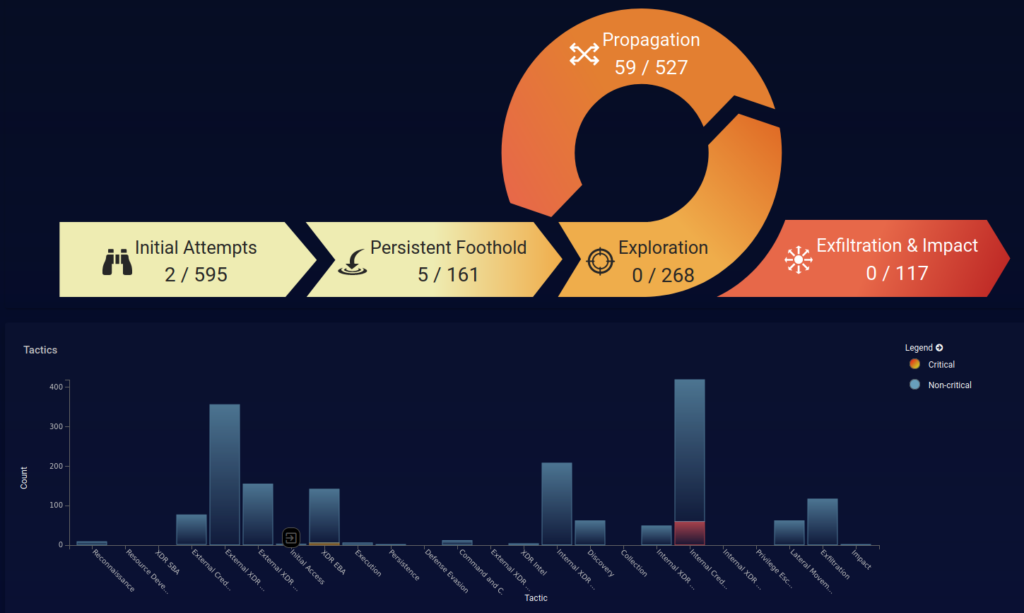
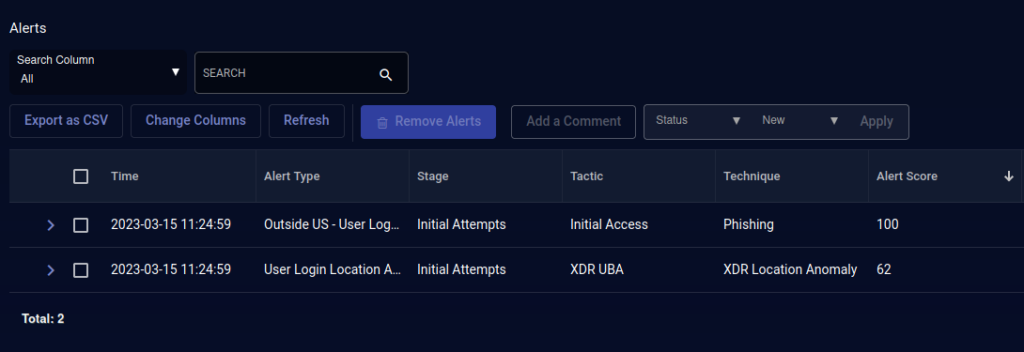
Network security is dramatically improved by bringing all that information under one roof and operationalizing around it. Imagine a staff member’s Office 365 credentials compromised through a phishing or watering-hole attack. Without a Security Operations Center, the alerts generated from Microsoft may be never seen. In one such scenario, Deeptree’s security team, Gray Raven, saw an alert from Microsoft that a client had logged in from Tirana, Albania. They had the client’s Operations Director on the phone within two minutes, validated this was not the staff member in question, rotated the password, and logged out the user (including the session the attacker was using) within five minutes. Many times those kinds of alerts indicate someone is on vacation. On rare occasions, it means something else altogether.
At Deeptree, our Security Operations Center is integrated and performed in-house to ensure maximum security through work efficiency, accountability, and knowledge of client workflows. Every morning, a Gray Raven staff member briefs the entire team of any active investigations underway, the results of any in-depth security activities performed (examples include vulnerability scans, threat hunts, and attack path management), and an overview of the global threat landscape.
Recently, Microsoft published an update to a critical vulnerability that allowed an attacker to steal credentials by inserting a malicious parameter into an email, calendar invite, or tasks. This critical vulnerability was used by attackers for 11 months before a patch was delivered. While automated updates help bridge the gap between the latest code and what is running on our computers, it does not bridge the gap between the latest attacks and the latest code. Security Operations Centers do.
So when a Deeptree staff taps on the shoulder of a Gray Raven teammate at a moment’s notice if they see something suspicious, or a Gray Raven staffer digs into that weird process that just kicked off when that PDF file was opened up – it’s a virtuous cycle that produces real results. No ransomware events for Deeptree customers for the nearly ten years we have been in business. Security matters, and making sure stewardship of that security is integrated with all things IT is vital to success.
Want to learn more about how Deeptree can help protect you and your business? Drop us a line!
From the rookery at Deeptree,
Peter House

